Azure DevOps
By integrating Azure DevOps with DX, you can analyze pull requests, repositories, and pipelines data. Please refer to the API documentation below and our schema explorer to see what data DX imports—note that DX does not read or access your source code.
DX provides four separate connectors—for Boards, Pipelines, Repos, and Pull Commits—which must be configured independently with separate service accounts and API tokens in order to avoid rate limit issues.
Prerequisites
To connect ADO to DX, you need:
- an ADO service account
- personal access token (PAT) with expiration date
Setup instructions
Follow the steps below to connect Azure DevOps to DX.
Data connection
Step 1
- Go to the Azure portal and create a service account in Microsoft Entra ID (formerly Azure Active Directory).
- Then, assign the service account to an ADO organization and grant them permissions.
- See Add organization users and manage access and Security groups, service accounts, and permissions reference for more information.
Step 2
- Log into ADO using the service account
- Generate a Personal Access Token with the read permissions outlined below:
| Connection Type | Permissions |
|---|---|
| ADO Boards | - Work Items (read) - Graph (read) - Identity (read) - Project and Team (read) - Release (read) - Task Groups (read) |
| ADO Pipelines | - Build (read) - Graph (read) - Identity (read) - Project and Team (read) - Release (read) - Task Groups (read) |
| ADO Repositories | - Code (read) - Graph (read) - Identity (read) - Project and Team (read) - Release (read) - Task Groups (read) |
| ADO Pull Commits | - Code (read) |
| ADO Commits (Default branch) | - Code (read) |
Step 3
- Navigate to the connections page in DX and select “+ Connection” in the top right.
- Enter the credentials you have generated in the previous steps—refer to the information below for errors and troubleshooting.
Webhooks
DX supports Azure DevOps webhooks ingestion to sync pull request data in real-time. This is recommended in order to ensure real-time data accuracy in DX.
You can enable webhooks via the Azure DevOps API, or through the UI.
API-based setup
Run the CURL command three times for each project where you want to enable webhooks—once each for git.pullrequest.created, git.pullrequest.updated, and git.pullrequest.merged:
curl --location 'https://dev.azure.com/${your_organization}/_apis/hooks/subscriptions?api-version=7.1' \
--header 'Authorization: Basic ${token}' \\
--data-raw '{
"consumerActionId": "httpRequest",
"consumerId": "webHooks",
"consumerInputs": {
"url": "${your_url}/webhooks/ado",
"httpHeaders": "X-ADO-Signature:${webhook_token}" # Replace this token with webhooks secret from DX, found on the Connections admin page
},
"eventType": "git.pullrequest.created",
"publisherId": "tfs",
"publisherInputs": {
"repository": "",
"branch": "",
"pullrequestCreatedBy": "",
"pullrequestReviewersContains": "",
"projectId": "${project_id}",
},
"resourceVersion": "1.0",
"scope": 1
}'UI-based setup
To enable webhooks via the UI:
- Navigate to Project Settings > Service Hooks
- Click the ”+” icon and choose Service “Webhooks” to add a new webhook.
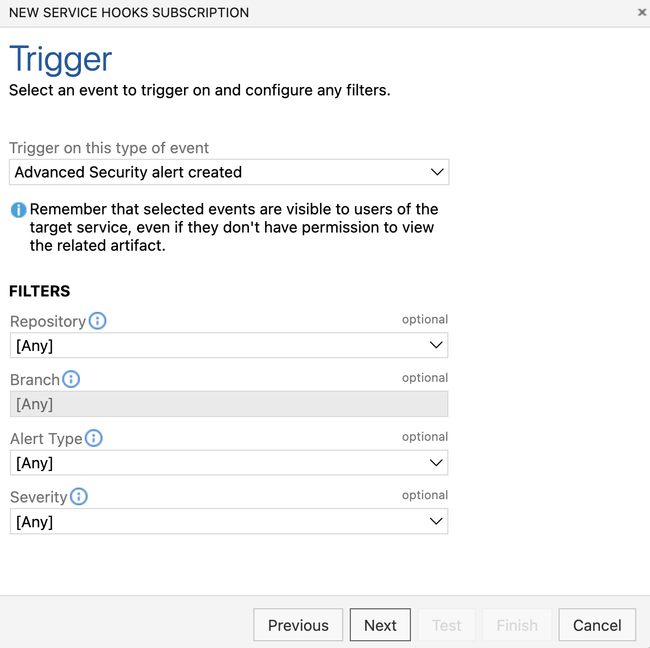
- Here’s what your settings should look like:
API reference
The table below lists the specific API endpoints that are used by DX.
| Endpoint | Documentation |
|---|---|
| /graph/users | Link |
| /projects | Link |
| /projects/{projectId}/teams | Link |
| /projects/{projectId}/teams/{teamId}/members | Link |
| /wit/classificationnodes/iterations | Link |
| /wit/workitemtypecategories?project= | Link |
| /wit/workitemtypes?project= | Link |
| /wit/fields?project= | Link |
| /wit/wiql | Link |
| /wit/workitemsbatch | Link |
| /wit/workitems?ids= | Link |
| /wit/workitems/{workItemId}/updates | Link |
| /build/builds?project= | Link |
| /build/builds/ | Link |
| /build/builds/{buildId}/timeline | Link |
| /release/releases?project= | Link |
| /release/releases/ | Link |
| /git/repositories?project= | Link |
| /git/repositories/{repoId}/pullrequests | Link |
| /git/repositories/{repoId}/pullrequests/ | Link |
| /git/repositories/{repoId}/pullrequests/{id}/iterations | Link |
| /git/repositories/{repoId}/pullrequests/{id}/iterations/{id}/changes | Link |
| /git/repositories/{repoId}/pullrequests/{id}/commits | Link |
| /git/repositories/{repoId}/pullrequests/{id}/threads | Link |
| /git/repositories/{repoId}/pullrequests/{id}/workitems | Link |
| /git/repositories/{repositoryId}/commits | Link |
Curl commands
When DX verifies an Azure DevOps connection, it checks specific endpoints to ensure proper access. If your connection is failing, you can test these endpoints directly using the curl commands below to troubleshoot the issue.
Replace YOUR_ORGANIZATION and YOUR_PAT with your actual values before running these commands.
1. Test Project Access (Common for all connection types)
This verifies that your service account can access project information:
curl -u :YOUR_PAT -H 'Accept: application/json' 'https://dev.azure.com/YOUR_ORGANIZATION/_apis/projects?api-version=7.0'2. Test User Access (Common for all connection types)
This verifies that your service account can access user information:
curl -u :YOUR_PAT -H 'Accept: application/json' 'https://dev.azure.com/YOUR_ORGANIZATION/_apis/graph/users?api-version=7.0'3. Test Repositories (For ADO Repos connection)
Replace YOUR_PROJECT_ID with a valid project ID to verify repository access:
curl -u :YOUR_PAT -H 'Accept: application/json' 'https://dev.azure.com/YOUR_ORGANIZATION/_apis/git/repositories?projectId=YOUR_PROJECT_ID&api-version=7.0'4. Test Build Pipelines (For ADO Pipelines connection)
Replace YOUR_PROJECT_ID with a valid project ID to verify pipeline access:
curl -u :YOUR_PAT -H 'Accept: application/json' 'https://dev.azure.com/YOUR_ORGANIZATION/_apis/build/builds?projectId=YOUR_PROJECT_ID&api-version=7.0'5. Test Work Items (For ADO Boards connection)
This verifies that your service account can access work item types:
curl -u :YOUR_PAT -H 'Accept: application/json' 'https://dev.azure.com/YOUR_ORGANIZATION/_apis/wit/workitemtypes?project=YOUR_PROJECT_ID&api-version=7.0'6. Test Pull Request Commits (For ADO Pull Commits connection)
Replace YOUR_PROJECT_ID and YOUR_REPO_ID with valid IDs, and YOUR_PULL_REQUEST_ID with a valid pull request ID to verify pull request commits access:
curl -u :YOUR_PAT -H 'Accept: application/json' 'https://dev.azure.com/YOUR_ORGANIZATION/_apis/git/repositories/YOUR_REPO_ID/pullRequests/YOUR_PULL_REQUEST_ID/commits?api-version=7.0'7. Test Default branch Commits (For ADO Commits (Default branch) connection)
Replace YOUR_ORGANIZATION, YOUR_PROJECT_ID and YOUR_REPO_ID with valid IDs, to verify commits access:
curl -u :YOUR_PAT -H 'Accept: application/json' 'https://dev.azure.com/YOUR_ORGANIZATION/YOUR_PROJECT_ID/_apis/git/repositories/YOUR_REPO_ID/commits'If you receive a 401 Unauthorized error, your credentials are invalid. If you receive a 403 Forbidden error, your token doesn’t have the required permissions. If you receive a 404 Not Found error or empty results, check that your organization name is correct.
Note about Authentication: The -u :YOUR_PAT flag uses curl’s built-in basic authentication with an empty username and your Personal Access Token as the password. This automatically handles the Base64 encoding required for Azure DevOps authentication.
Errors
The table below lists potential error codes when adding a connection in DX.
| Error | Description |
|---|---|
invalid_credentials |
Your API credentials entered are not valid. |
invalid_permissions |
Your API token does not have the permissions required by DX. |
no_resources |
DX cannot access any projects or repositories. |